Overview of RBAC
The Ditto portal provides the ability to create, modify, and delete custom roles, allowing you to set fine-grained read-write access controls to app data. With this you can define organization hierarchies for permissions delegation, set permissions for portal functionality like viewing collections, querying tokens, transferring apps between organizations, and more.Organization Permissions Settings
When configuring access control for roles within an organization, there are various types of privileges you can choose from. These can be accessed from the role editor, available under Settings > Roles. The following table provides an overview of the various settings you can configure for roles within an organization.Some permissions have dependencies on others.For example, a role with Accept incoming app transfer requests permission will also have View incoming app transfer requests.Where this applies, these dependent roles will be selected automatically for you when selecting in the role editor.
| Setting | Description |
|---|---|
| Accept incoming app transfer requests | Initiate, approve, or cancel requests to transfer apps between organizations |
| Access audit logs | Review audit logs |
| Create an app | Set up new apps |
| Manage organization members | Oversee and administer the membership of an organization |
| View organization details | Access and view details related to the organization |
| View incoming app transfer requests | See requests from other organizations to transfer apps into the organization |
| Reject incoming app transfer requests | Decline requests from other organizations to transfer apps to the organization |
| Update the organization details | Modify information related to the organization |
| View access grants | Review the permissions granted to specific users, roles, or organizations |
| Manage access grants | Control and administer access privileges granted to other roles within the organization |
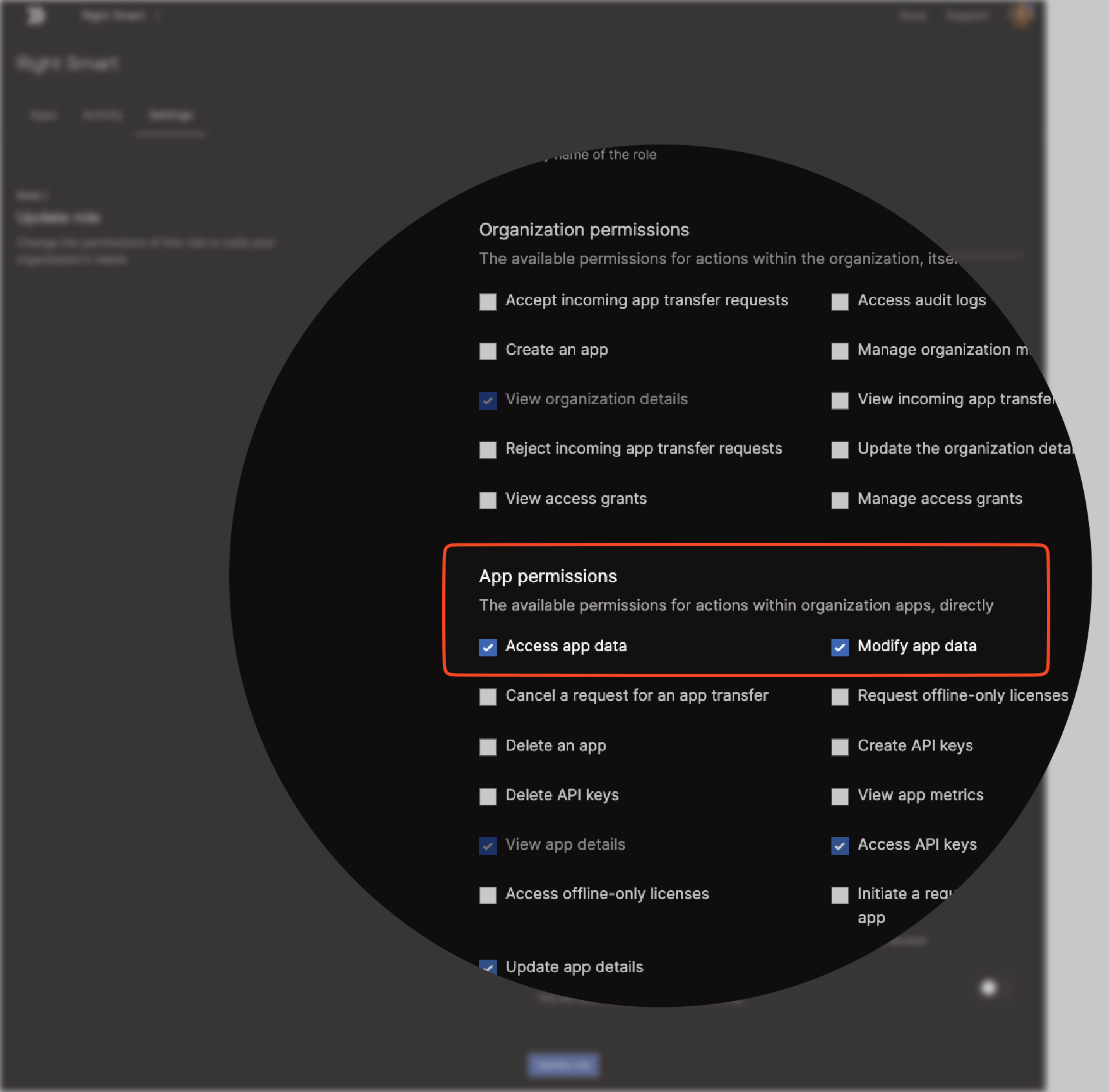
App Permissions Settings
Following is an overview of the various settings that, once assigned, grant end users the ability to manage the app. (See Creating Roles)| Setting | Description |
|---|---|
| Access app data | Access mesh-generated transactional data |
| Modify app data | Make changes to mesh-generated transactional data |
| Access app data bridges | Access CDC Data Bridges and their connection info |
| Manage app data bridges | Create, update and delete CDC Data Bridges |
| Cancel a request for an app transfer | Withdraw active requests to transfer apps to other organizations |
| Request offline-only licenses | Manage the licenses designating apps for offline usage |
| Delete an app | Permanently remove apps |
| Create API keys | Generate unique identifiers used for authentication and authorization access to app data |
| Delete API keys | Revoke authentication and authorization to access to app data |
| View app metrics | Review various analytics associated with apps |
| View app details | Access and review specific information and settings associated with apps |
| Access API keys | View the API keys used for authentication and authorization to access app data |
| Access offline-only licenses | View the licenses designating apps for offline usage |
| Initiate a request for the transfer of an app | Transfer ownership of apps to other organizations |
| Update app details | Modify the information and settings associated with apps |
| Access a MongoDB connector | Access the MongoDB connector configuration |
| Manage a MongoDB connector | Make changes to the MongoDB connector configuration |
Organization Roles
To establish role-based access controls for your organization:Create new roles with the desired settings. (Creating New Roles)
Designate roles for the appropriate end users within your organization. (Assigning Roles to End Users)
Creating New Roles
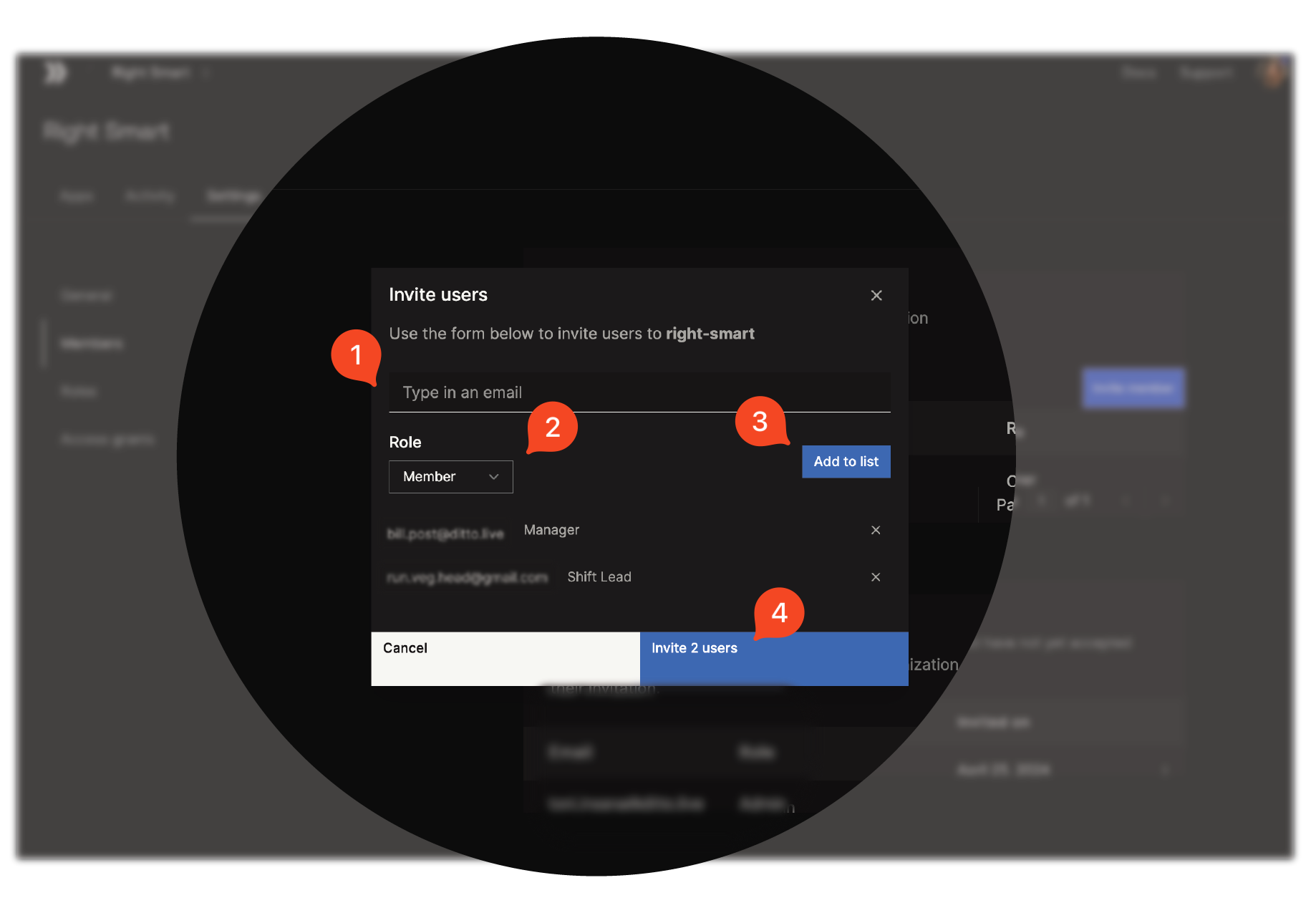
To add a new role to your organization:Assigning Roles to End Users
Once you’ve created a role, designate them to the appropriate end users within your organization:Viewing Pending Member Invitations
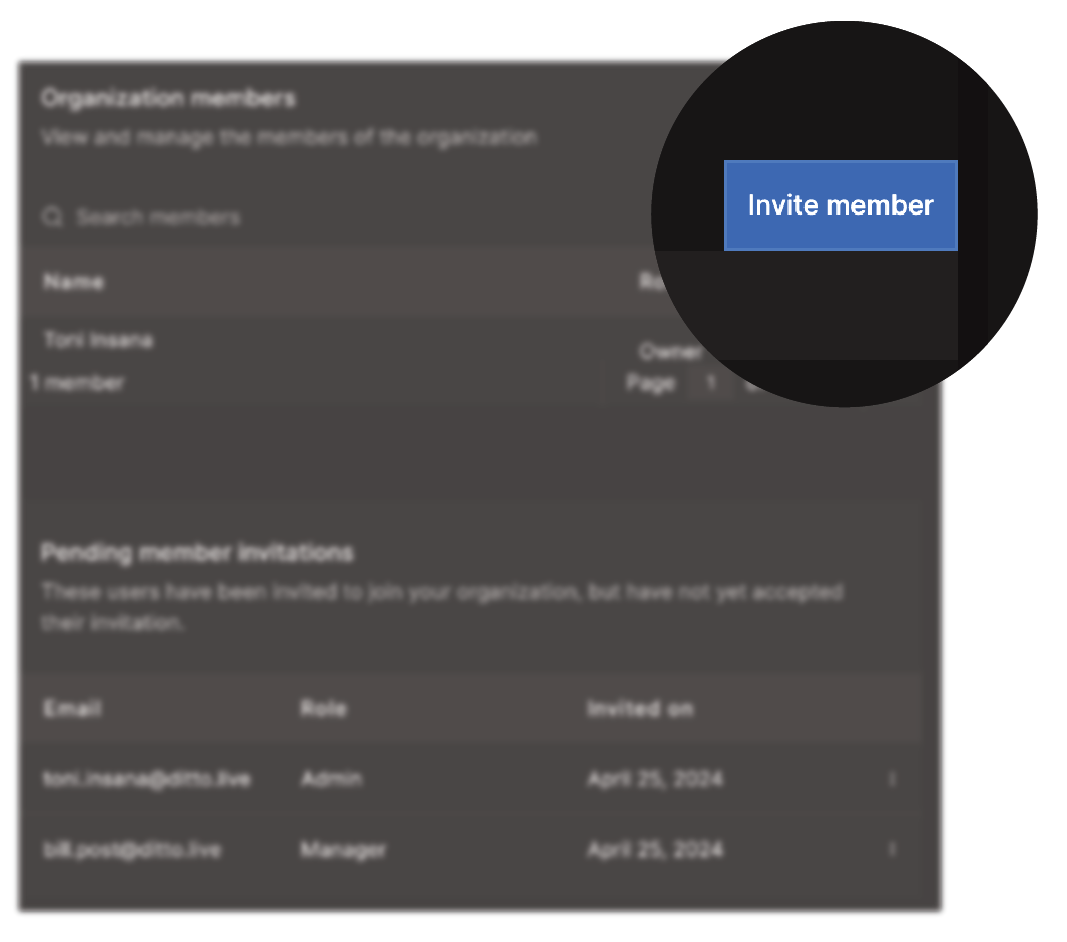
Once a member is assigned a role, Ditto automatically sends a formal invitation to the email address specified in the invite, which must be accepted before RBAC privileges take effect. To view a list of invitations waiting for approval, go to Settings > Members in the portal. A complete list of invitations display within Pending member invitations, as shown in the following graphic: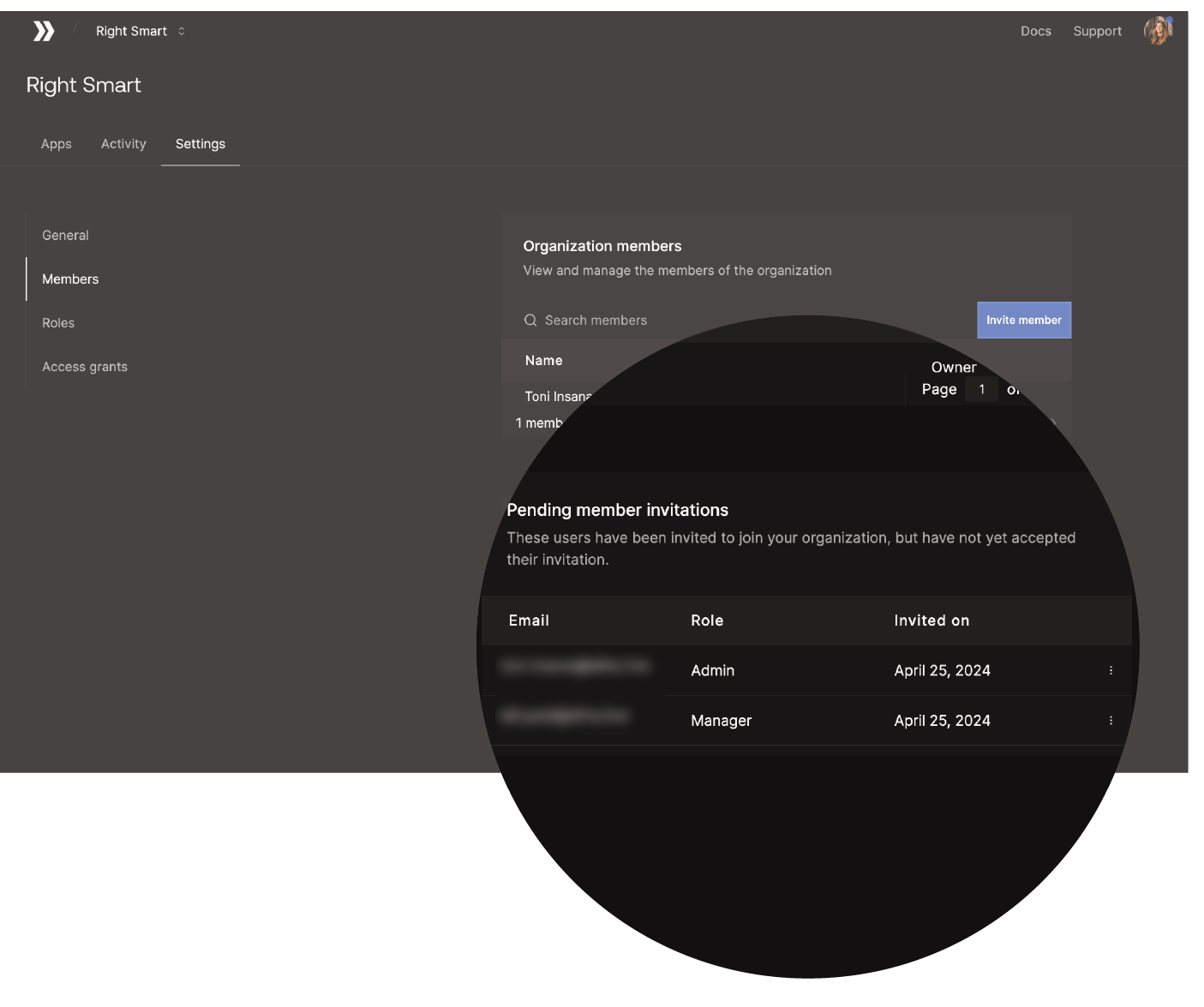
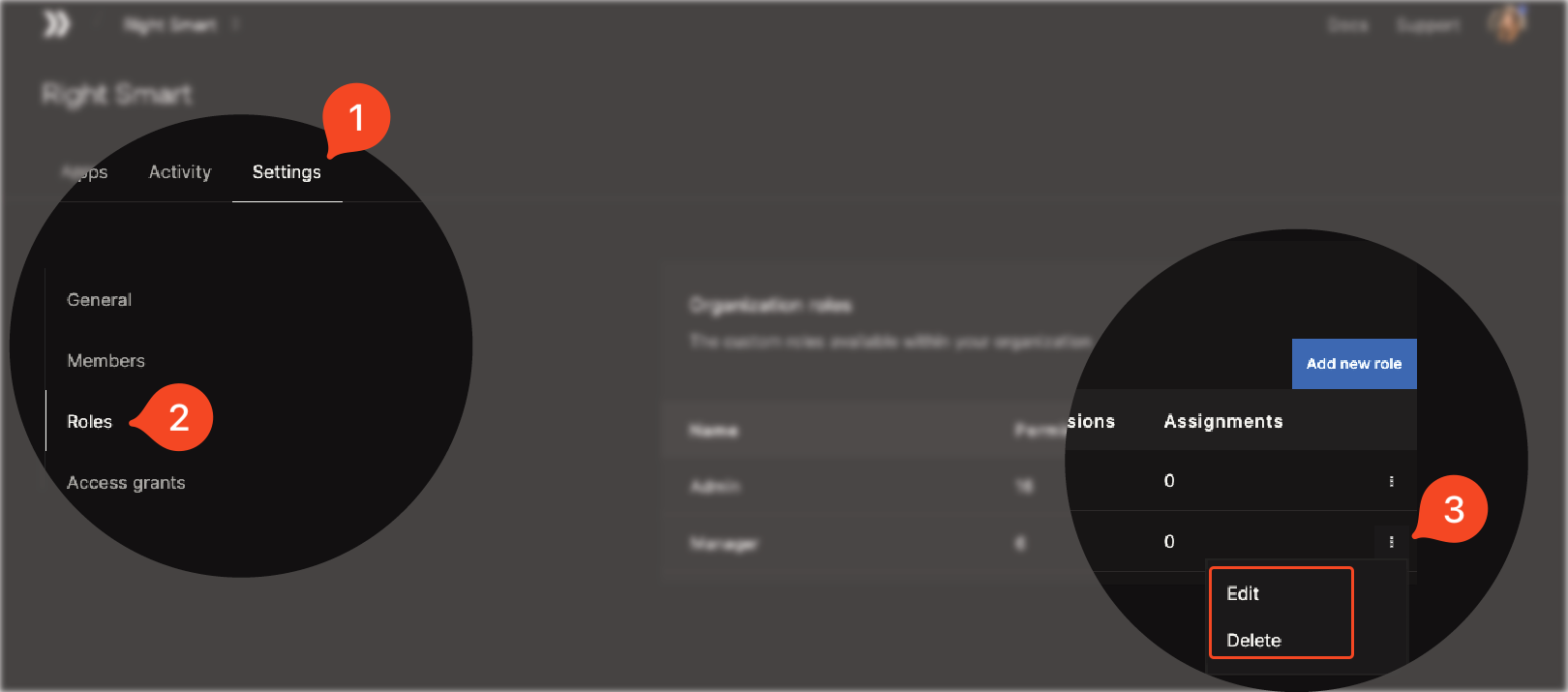
Modifying and Deleting Roles
To edit a role’s settings or permanently remove a role from your organization:Ditto Employee Access Grants
There are circumstances in which Ditto’s support team requires elevated privileges to access your app data, for instance, to troubleshoot an issue. Ditto employees can only access your app data with an approved access grant. An access grant is a formal authorization provided by any of the following to approve the access request initiated by Ditto:- Current organization owner
- Organization roles configured with** Manage access grants** privileges