Key Benefits
- Fully Managed Service: Ditto’s engineering experts handle all day-to-day operations and infrastructure maintenance.
- Complete Control: Maintain full control over your cloud infrastructure and security policies.
- Enterprise-Grade Security & Data Sovereignty: Your customer data remains within your own cloud environment.
- Cost Optimization: Leverage existing cloud provider discounts for a lower Total Cost of Ownership (TCO).
Architecture
Ditto Server Components
Ditto Server is built with a microservice architecture running on Kubernetes, providing maximum scalability and fault tolerance. The system includes:- Subscription Server: Syncs data to and from devices connected via the Ditto SDK
- API Server: Serves the Ditto Server HTTP API
- Store: The data store layer
- Authentication Service: Manages device authentication
- Change Data Capture: Exposes data changes to external systems
BYOC Deployment Model
The architecture for BYOC consists of two main components: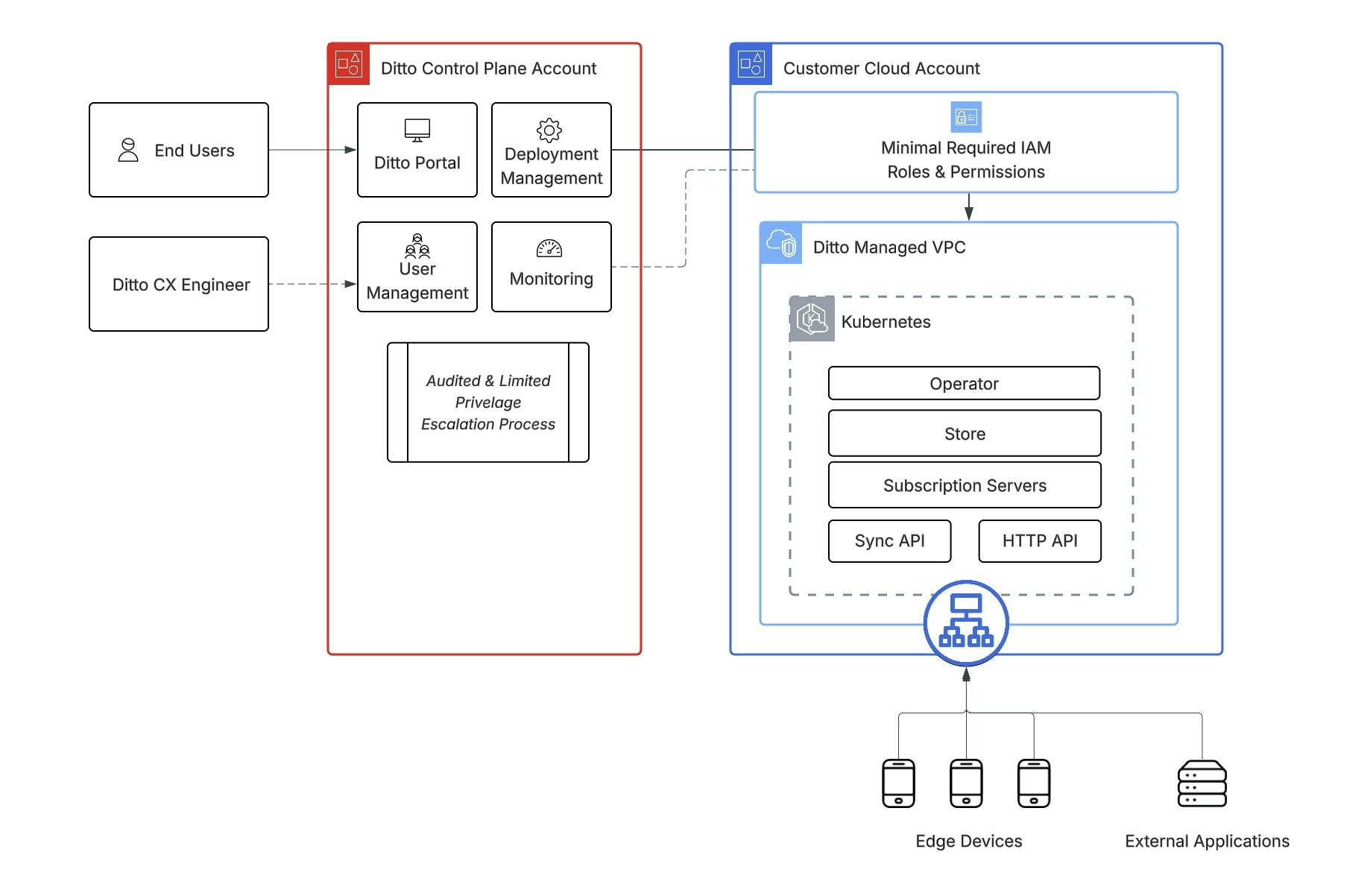
Control Plane (Ditto’s Cloud Account)
The Control Plane consists of a number of services run by Ditto, hosted in Ditto’s own cloud account. Its purpose is to automate the management of Ditto Server running in the Data Plane (in the customer’s account), to eliminate the burden of ongoing infrastructure maintenance. The Control Plane is responsible for a number of functions, including:- Deploying Ditto Server into the Data Plane
- Orchestrating Ditto Server maintenance and upgrades
- Monitoring and alerting for Ditto Support and Engineering, to ensure ongoing reliability
- Providing end-user access to apps deployed on the Ditto Server, through Ditto’s portal
- Ditto Portal user management, RBAC, and SSO
Data Plane (Customer’s Cloud Account)
The Data Plane resides in the customer’s own cloud account. This is where Ditto Server itself is deployed, and therefore where data resides and where clients connect. It consists of:- IAM roles with scoped permissions to enable the Control Plane to manage Ditto-deployed resources within the account
- A VPC, which can be created by Ditto during the account provisioning process, or provided by the customer
- A Kubernetes cluster, in which Ditto Server is deployed
- Ditto Server, which consists of a number of microservices deployed on Kubernetes
- Various associated components deployed within the VPC to enable connectivity to Ditto Server, such as load balancers, subnets, and security groups
Sizing and Scaling
Ditto offers flexible deployment options designed to grow with your application needs. Our managed infrastructure automatically scales to handle varying workloads while maintaining optimal performance. Choose from three pre-configured deployment shapes, each optimized for different use cases:- v1-Small - Ideal for development, testing, and small production deployments
- v1-Medium - Recommended for growing applications with moderate traffic
- v1-Large - Built for high-traffic production environments requiring maximum performance
Auto-Scaling and High Availability
All deployment shapes include built-in auto-scaling capabilities with sensible default limits to handle traffic spikes automatically. For production workloads requiring zero-downtime operations, high availability is available with v1-Medium and v1-Large shapes, providing redundancy and fault tolerance. Start with Ditto’s default (“v1-small”) cluster. Ditto will help adjust sizing as you grow your production workloads.- Key components scale independently:
- API Server: For app traffic.
- Subscription Server: For device connections.
- Store: For high-volume data or redundancy.
Shared Responsibility Model
Security and Compliance
Since Ditto on public cloud runs in a customer’s cloud account, security and compliance is a shared responsibility between Ditto and its public cloud customers.Day-to-day management of infrastructure deployed within the customer’s Data Plane will be handled by Ditto’s Control Plane, however there are some shared responsibilities given the nature of being deployed in the customer’s account.
| Customer | Ditto | |
|---|---|---|
| Cloud Infra | - Provide sub-account and IAM permissions in chosen provider - Select cloud provider and region when creating new deployment - Adjust service quotas if and where necessary | - Provision new deployments in dedicated VPC - Provision required supporting services - Apply configuration changes without service disruption - Automatically scale infrastructure as required for customer workload |
| Customer Data | - Provide and manage customer data - Maintain cloud user accounts and sensible access policies | - Provide secure access to customer data - Provide APIs and SDKs to store and retrieve data securely |
| Deployment & Sizing | - Provide information about intended usage to Ditto for sizing recommendations | - Provision deployments with best-practice sizing according to customers needs - Proactively re-size deployments in response to changes in demand |
| Database Access | - Maintain auth webhook used to control access - Configure HTTP API access keys | - Maintain always-on authentication forwarding to the customer’s authentic webhook |
| Portal Access | - Manage access - users and permissions - Configure SSO | - Maintain always-on authentication - Provide SSO integrations with external authentication providers - Provide native MFA capability |
| Data Encryption | - Ensure data is always encrypted in transit - Ensure all provisioned disks are encrypted using CSP-provided encryption | |
| Data Locality | - Choose region and provider - Understand and comply with data locality regulations | - Support multiple regions and cloud providers - Ensure all customer data remains in the deployment region |
| Security patches and maintenance | - Provide desired maintenance window to Ditto | - Apply platform software upgrades - Apply security patches to supporting infrastructure - Follow customer’s desired window, where possible |
| Intrusion Detection | - Monitor cloud provider account for intrusions | |
| Monitoring and alerting | - Monitor for cloud provider-specific issues | - Collect monitoring metrics - Proactively monitor platform health metrics |
| Backups | - Periodically take backups - Ensure backup retention | |
| Remediating availability issues | - Contact cloud provider support for cloud-level issues, if directed by Ditto support - Make cloud-level changes if requested by cloud provider | - Proactively remediate availability issues caused by Ditto software - Instruct customer when to contact their cloud provider’s support to remediate an issue |
Operations & Support
- All deployments run in high-availability mode (multi-AZ) wherever possible.
- Ditto handles monitoring, upgrades, health checks, and incident response.
- Your team has access to usage metrics and support through the portal.
- Ops team coverage is 24/7 for all managed environments.
Upgrades and Maintenance
Ditto will perform necessary upgrades to the Ditto Server and underlying Kubernetes infrastructure to ensure all deployments receive the latest features, security patches and reliability improvements. Upgrades are typically carried out on a monthly cadence, but can vary depending on Ditto’s feature release schedule and the need for infrastructure maintenance. New releases of Ditto Server are published in our release notes: https://docs.ditto.live/cloud/release-notes Customers can supply Ditto with a preferred maintenance window in which we will aim to perform any upgrades and maintenance. In almost every instance, this window can be respected, but in exceptional circumstances Ditto may take immediate action outside of this window to roll out urgent fixes or security patches.FAQ
How do I get started?
How do I get started?
Contact sales via ditto.com for guided onboarding.
Do I need to manage Kubernetes?
Do I need to manage Kubernetes?
No - Ditto fully manages K8s infrastructure in your cloud account.
How does Ditto access my environment?
How does Ditto access my environment?
Via narrowly scoped IAM roles needed for deployment and management. No persistent admin access.
Can I use BYOC in multiple regions?
Can I use BYOC in multiple regions?
Absolutely. Tell your onboarding team about your requirements.
For setup requests or technical questions, please contact support.